The top reasons why outsourcing is an excellent choice
Here are the top reasons why outsourcing is an excellent choice for seeking speed and quality innovation.
1. A vast pool of skilled resources
It may be challenging to identify or educate in-house specialists with a wide range of talents, but outsourcing gives access to a big pool of them.
2. Expertise of outsourcing providers
It has a distinctive background dealing with a range of industries and technology. Over time, this increases their level of knowledge and expertise to make things fast and avoid inventing of bicycle.
3. Exceptional Time-Saving
By using outsourcing, you may quickly add the essential talents to your team. Saving time is a big competitive advantage for the expansion of a business.
4. Flexibility
It enables you to handle brief or minor activities in your workload swiftly and effectively without spending excessive money on hiring and terminating employees to complete the same duties.
5. Risk Reduction
A trustworthy outsourcing partner will act as an extension of your team, alerting you to potential dangers in the market and guaranteeing the safety of any necessary technical infrastructure.
6. Continues workflow
Because of the time difference, the work may be done and the problems can be solved overnight.
7. Scalability
Short-term outsourcing is useful when a project requires more manpower or space. Since there are no binding contracts to sign.
8. Lower cost
In most cases, outsourcing will save you money.
How Zeus Created a Trusted Path to Innovation and Growth:
In today’s competitive business landscape, companies must constantly seek new ways to innovate, access specialised expertise, and control costs. Outsourcing has emerged as an appealing solution, providing access to a global pool of talent and enabling companies to focus on core competencies.
As an established outsourcing provider, Zeus understands what it takes to build successful, secure partnerships. With over a two decades of experience across various industries, Zeus has honed its ability to deliver excellence efficiently taking under consideration culture code, client’s current needs and constrains.
The Zeus Advantage
- Deep expertise in the latest technologies and methodologies
- Stringent vetting and training of all experts
- Robust cybersecurity infrastructure and protocols
- Award-winning project management practices
- Flawless track record of on-time, on-budget delivery
- Clear communication and transparency at all levels
- Customised engagement models to match unique business needs
- Specially designing pricing models which deliver outstanding results for MVP ideas, startups and small and medium businesses
By outsourcing to Zeus, partners gain an extension of their team with proven expertise and are able to make short term assignments via Zeus resource pool service. Zeus takes care of the heavy lifting, so you can focus on your core business goals.
Steps to help you identify the need for outsourcing:
First, you should evaluate your company’s requirements by distinguishing between “core” and “support” business processes. Keep in mind that your core essence makes your business unique.
Second, take a look at what you already have: assess whether or not your organisation has the resources to carry out the tasks you’ve outlined. The employees, abilities, and tools at your disposal must all be evaluated.
Third, calculate what it would cost to do the work in-house: Consider how much it would cost to bring the work in-house, including salaries, benefits, and the cost of any necessary equipment.
Weigh the advantages of outsourcing against its expenses. Weigh the benefits of outsourcing, such as getting access to specialised skills and saving money, against the costs of doing the work in-house.
Fifth, think about other things: The possible impact on operations and personnel, as well as legal and regulatory issues, should be considered when considering whether to outsource.
Outsourcing can take several forms, such as One definition of manufacturing outsourcing is contracting with a third party to produce goods on an organisation’s behalf.
Second, when a business outsources its IT, it employs an outside company to care for its computer networks and related services.
Third, a company may use business process outsourcing to have tasks like payroll, accounting, and customer support handled by an outside company. Human resource outsourcing is the practice of contracting with an outside company to manage HR-related tasks in-house, such as benefits administration and regulatory compliance.
The fifth type of business process outsourcing is legal outsourcing, in which a company contracts with an outside firm to manage a company’s need for legal services.
When you outsource your marketing, you provide duties like social media management and content development to an outside company.
Both large and small businesses use outsourcing. They may outsource all or most of their operations to concentrate on running the firm.
Both scenarios call for people to review a few essential details that will allow them to make a well-informed choice.
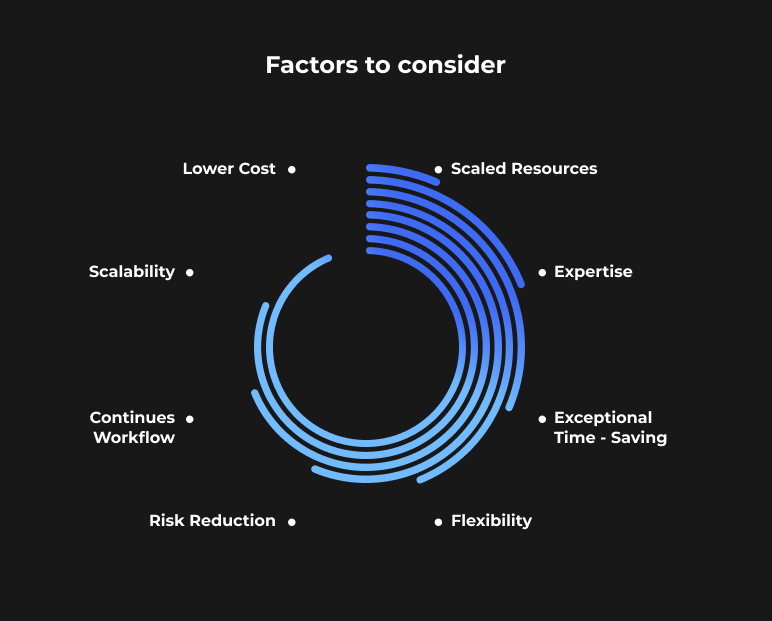
Factors to consider when making outsourcing decisions for your business

Let’s take a look at some of the things that matter when you’re deciding whether or not to outsource for your company.
1. Reduced Expenditures
If you want outsourcing to be profitable for your company, it should help you save money on overhead. You’re more likely to overspend than save if you don’t anticipate this happening anytime soon. You don’t have to be a rocket scientist to predict your future. The only thing you need to check is whether or not outsourcing will help you save a tonne of money on staff and tools.
In addition, you need to know exactly how much money you have set out for outsourcing software development. Suppose you wish to build a new product or compare the operating expenses necessary to sustain or modernise a current one. In that case, this will affect the location for outsourcing, the business model, and the quality of the final product.
2. Time-management skills
When outsourcing, speed is just as important as low prices. For instance, significant delays may result from a vendor’s failure to meet their commitments. Just that one thing will cancel out whatever savings you expected from employing them. You need to make sure the supplier delivers on schedule and as promised. Preparing questions in advance is one strategy for this.
3. Reduce Risks and Obligations
There is a higher likelihood of liability accumulation in some company functions. This wastes resources that could be used elsewhere. You can cut down on your legal obligations by outsourcing some tasks.
4. Reliability
Make sure you check out the vendor’s website before signing anything. You should also look into the company online to learn more about its operations, facilities, safety procedures, and staff. You may use this information to gauge the trustworthiness of the service providers. A third option is to inquire with a reference who has prior experience working with the vendor about their opinion of the company. That brings us to our next topic. Keep an eye on the software engineers’ technology stack. Make sure your vendor has experience in the target sector, as there are many specialised outsourcing providers who generate amazing goods for a certain niche. Think about what other companies have said about their outsourcing experiences. You may learn a lot about your vendor’s ethics (and whether or not they deliver on commitments) by reading reviews online.
5. Expression of Ideas
Working onshore or with an offshore team, communication is essential. You shouldn’t have to wait forever for a response to your questions from the suppliers. There can be no room for cultural or other communication hurdles in their communication abilities. In this way, you know they fully grasp your specifications and can deal with any difficulty that may arise.
6. Security
Make sure that there are security clauses in the contract to protect your trade secrets. Also, make sure the data transfer processes are secure to your liking.
7. Risks
Some dangers may be included while outsourcing. Potential challenges include, but are not limited to, unanticipated expenses, substantial cultural gaps, and ongoing delays. Preparedness and stringent terms in the contract can help reduce the impact of the risks. You might also decide against outsourcing anything and instead staff an in-house ODC with developers that share your company’s values and ethos.

8. Time difference
Be sure to plan ahead when outsourcing product development overseas to avoid scheduling conflicts. Make sure the time difference won’t slow you down (or figure out how to exploit it to your advantage).
Yes! When opposed to employing internally, outsourcing provides a number of benefits. The problem with relying on an internal staff, however, is that it takes a lot of time and money to really implement any ideas that are conceived. The ability to move quickly, adapt your strategy as needed, and grasp opportunities as they present themselves are all benefits of outsourcing.
With your own ODC, you can expect to: Get developers that are only focused on your product; Have direct access to the team to ensure they are adhering to your processes and policies; Set your KPIs and have complete control over the activities and outcomes.
Advantages of the Safe Outsourcing Concept
1. Trusted Expertise:
Zeus brings a wealth of knowledge and experience to the table, ensuring that your projects are handled by experts who understand the intricacies of your industry and technology.
2. Risk Mitigation:
Zeus’s focus on robust cybersecurity and risk management practices keeps your organization’s sensitive data and infrastructure secure.
3. Rapid Innovation:
By leveraging Zeus’s expertise and resources, you can accelerate your innovation initiatives and stay ahead of the competition.
4. Scalability:
The concept offers flexibility to scale your projects up or down according to your specific needs without the constraints of binding contracts.
5. Cost Savings:
Outsourcing to Zeus typically results in cost savings, making it an economically attractive option for businesses of all sizes.
How Safe Is IT Outsourcing?
Investing in study, project management, digital transformation, and security measures may make IT outsourcing a highly secure option. Significant cost savings, enhanced quality of service provided to customers, and the ability to bridge skill shortages by drawing from a larger talent pool… The examples are endless. Numerous arguments point to the importance of offshore software development hubs in the current era of digital transformation. But how risky is it to hire workers in another country? While it may seem easier to plan and supervise an in-house staff, the reality is that IT outsourcing may be lucrative and secure with little effort on your part.

Research potential partners
Do your research beforehand to avoid any unpleasant surprises. Partnerships in Eastern Europe are generally seen as safer than those in Asia, Latin America, or Africa, the three other major outsourcing destinations. Countries like Bulgaria, Romania, Croatia, Slovenia, Slovakia, and the Czech Republic are prime examples of this trend among EU members. More openness and standard IT compliance are the results of government policies and business rules that are similar to those in the West. Better conditions, including increased political and financial stability, always have a positive impact on the standard of goods and services offered.
Because of the time difference, corresponding with the United States is more difficult. Even so, it’s a significant plus when the offshore development centre is just seven to ten hours ahead of your own (as in Eastern Europe), allowing you to assess the day’s work right when your business day begins. Once you’ve decided on a location, it’s time to do some digging on the major players there. Check out how they’re rated on unbiased review sites like Clutch to learn more. You should also look at the portfolios for projects that are comparable, as this will help you find specialists who can help speed up your business’s operations and boost the quality of your final output. Then, inquire for recommendations, since current or past business associates can comment on the service provider’s genuine collaboration and any hazards involved.
Project management is a key
Since meeting your quality and safety standards depends on the project running smoothly from start to finish, excellent project management is essential. That’s why it’s important to lay out the ground rules for the whole partnership. Complete documentation of the Scope of Work is essential. This includes the budget, volume, timeline, milestones, and deliverables. The same holds true for technological standards, which is why the CTO of the firm must be involved in their creation.
The success of the project hinges on the team’s ability to plan and communicate effectively. By keeping everyone informed, mistakes may be caught before they spiral out of control, saving time and money. It’s never a good idea to rewrite code close to or after the project’s conclusion.
Scaling Capability and Capacity When You Need It
Since these choices help you enhance project management procedures and delivery, optimise costs, advance communication and reporting, and encourage team morale, you need to think about the maturity of your organisation and look at flexible service models to meet your project development demands. Our experts can assist you in reaching your goals, whether you require regular support or aid with a single project.

Invest in Digital Transformation
Without a digital transformation strategy, businesses struggle to adapt, lose their competitive advantage, and ultimately jeopardise their own long-term existence. It is the responsibility of service providers to help their partners overcome the challenges of digital transformation. An effective supplier will anticipate your wants and make suggestions for improvements in line with a well-defined innovation idea that incorporates the whole innovation cycle and a methodical approach to rewards.
Changes in the way data is collected, stored, analysed, and used are at the heart of digital transformation. Reorganising your data environment with the support of a development partner skilled in data and data science is the key to releasing the full potential of AI, ML, and Advanced Analytics. When it comes to data, ZEUS has the know-how to assist our partners get the most out of it.
Cybersecurity is paramount
Since more work is being done remotely, more digital work is being done more quickly, which increases the risk of cyberattacks. Businesses must revise their approaches to cybersecurity as they shift away from on-premises data storage and towards cloud- based ecosystems of linked apps. To meet the long-term needs of their customers, service providers must create innovative approaches to information security.
At the outset of any cooperation, both parties should have well-developed plans and vital cybersecurity compliance programmes to safeguard their most valuable assets. The loss of trust caused by the exposure of private information is bad for business, and the breach of critical company information can have catastrophic results. Companies with known vulnerabilities run the danger of severe fines and the loss of confidence and custom if a breach does occur.
This is why distributed software factories can’t use cutting-edge platforms that allow for continuous compliance upgrades and higher security. More than simply adhering to the internationally recognised best practices for IT risk management is required. Beyond the typical functional, end-to-end, and performance tests, there must also be testing for digital operational resilience.
Data Processing by a Third Party: Why You Should Care
Generally, there are three important aspects of data protection:
- availability;
- integrity;
- confidentiality.
All of them are impacted when one of them goes out of control. Processing of personally identifiable information that is not secure can lead to theft, financial loss, and damage to credibility. Because of this, you need to pay great attention to the assurances of data security provided by each outsourcing partner you choose.
Two groups of interested parties will now have their questions about “what is data processing?” addressed.
You, the business owner, are ultimately responsible for ensuring the security of your company’s data by selecting a trustworthy outsourcing partner. A reliable third party will take data security very seriously. They must specify the nature, purpose, and boundaries of their data processing operations. Your business associate has a legal obligation to protect any data subject to GDPR from disclosure. You can pick between an offshore, onshore, or nearshore business alliance.
Offshore suppliers are not in your immediate geographic region. The offshore partnership is a low-cost strategy for locating a reliable outsourced provider. Onshore businesses offer the convenience of having a partner located in the same nation as you. You can trust that your data is safer with an onshore partner. That is, if you are familiar with the legal system in your nation. An offshore partner in close proximity. Having a nearshore partner with a similar mindset is a huge plus. This leads to more fruitful commercial conversations and a shared comprehension of the project’s objectives. Who should I work with near shore? Consider the legal protections afforded to individuals in a nation before deciding to outsource there. Learn the numbers that pertain to a specific nation. Examine how often data breaches occur, how much they cost, and what effect they have in the area of interest. It will aid in locating a trustworthy outsourcing firm in the area, giving you peace of mind about the safety of your sensitive information.
You might, for instance, examine the sum total of GDPR fines imposed in specific nations between 2018 and 2020:
What does third-party data processing mean for a business owner?

What does data processing mean for an outsourcing partner?
Suppose Business A contracts Business B to create a customer relationship management system for their online store. Creating this type of system requires Company B to get sensitive information about its customers. When it comes to the security of their information, Company A is their “go-to” provider. Company B is expected to guarantee this for Company A. The two work together to secure data. The General Data Protection Regulation explicitly states that both parties must ensure the security of data processing.
What, therefore, can be done by an outsourcing partner themselves? Starting with the safety of the office is the first step in protecting sensitive initiatives. The outsourcing company’s data should be protected by the most stringent security measures possible. Testing for vulnerabilities and intrusions is a wonderful approach to see how secure an organisation is and where there may be holes.
They must also have a well-written privacy policy that specifies which third-party services can access their information and how. A Data Processing Agreement (DPA) must be finalised with each customer. Data processor definition will be provided in subsequent sections. Let’s analyse the necessity of DPA for our clientele now.
DPA as a Way to Keep Your Data Safe
Just what is DPA, anyway? The abbreviation for “Data Processing Agreement” is “DPA.” All data processing operations must conform to DPA guidelines to be considered GDPR-compliant. Data protection agreements (DPAs) ensure the security of project information and provide rules for minimising the risk of data breaches. How do you know whether you need a data processing agreement? When absolute confidence in the safety of your data is required. No specific form is associated with the data privacy agreement. This document may be written or electronic, and it may be an attachment to or a stand-alone from the main contract. What matters is how the parties really conduct themselves. DPAs (Data Processing Agreements) are effective regardless of how they are written. Its contents, however, do.
What DPA Should Look Like
If you were wondering, “What does DPA stand for?” now you know. Then, we’ll take a look at the DPA’s main ingredients. Depending on the issues, needs, and objectives of the parties involved, other ones may be added. Make sure the following are included in any Data Processing Agreement you sign with a third-party provider before committing to the partnership.
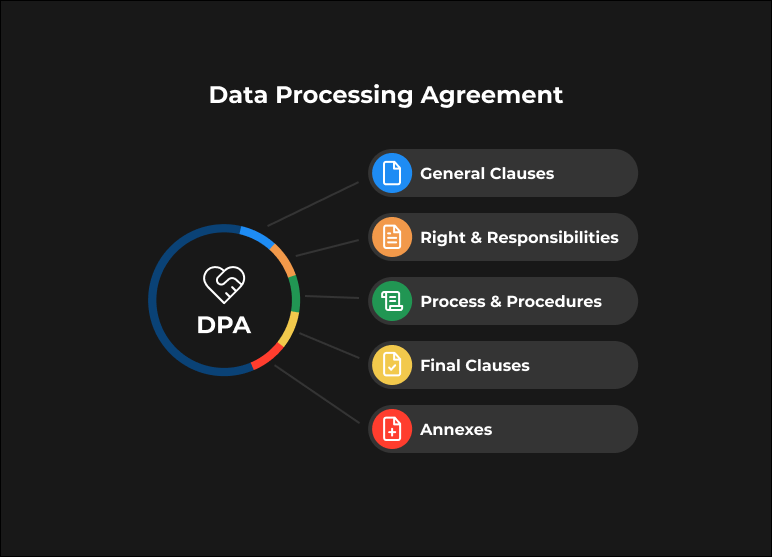
1. General clauses
Your DPA should include a list of who is:
- Data controller. Data controllers are stakeholders who entrust their data to a third party.
- Data processor. Then, what exactly is a data processor? The person or organisation that processes data on behalf of the data controller may be referred to as the data processor.
n addition, the initial portion of the text explains the following:
- Types of DPA data (data that will be accessed by a third party).
- Subjects of data. These latter may comprise a wide variety of groups of individuals or organisations whose data will be handled. This might refer to your company’s customers or partners, for instance.
The following should also be included in the description of general clauses:
- Goals of data processing.
- Scope of customer data.
- DPA software (data processing systems, tools, or software solutions).
- Duration of processing personal data (or enterprise data usage).
- Data storage description.
And how long will the DPA (data privacy agreement) be in effect? Describe in detail the following:
- Duration of the agreement.
- Conditions of agreement termination.
Do not forget to mention that personal data processor is obliged to remove your data from their storage once DPA is terminated. That is, data transferred to their systems have to be permanently deleted in this case.
2. Rights and responsibilities of stakeholders
This part consists of: • The rights and responsibilities of a data controller. • As the data controller for your organisation, your rights and obligations will be outlined in this section. Why are we even discussing responsibilities? Because the DPA stipulates that you are responsible for respecting the rights of data subjects and ensuring that a processor processes data in accordance with terms, processing instructions, and legislation, you are required to do so. Therefore, the obligations also fall on your shoulders. • The rights and responsibilities of a data processor. The rights and duties of data processors are laid forth in this section of the agreement. What exactly is it that a data processor does? Their primary responsibility is to remove the potential for a data breach while also ensuring the continuing security of the data. A data processor is obligated to provide you with an effective reaction in the event that the breach takes place. Companies that process data are obligated to respect the rights of the people whose information they handle.
A data processor is required to maintain a record of their data-related activities and provide you permission to do an audit to ensure that they are in compliance with the DPA. Without first obtaining your permission, they are not permitted to involve any third-party service providers in the processing of your data.
3. Procedure and process description
The third section discusses the precautions that were taken by all involved parties in order to protect personal information and carry out data processing in a risk-free environment. It is best to make mention of both of the following, if possible:
- Organisational aspect of data protection and agreement compliance.
- Technical side of the same aspect.
4. Final clauses
In this section, companies will often mention:
- Conditions under which the agreement can/cannot be changed.
- Data Processing Agreement superiority over other documents.
5. Annexes
Annexes include any supplementary documentation essential for the execution of Data Processing Agreements. For example:
- Tables with step-by-step process descriptions.
- Audit results.
- Lists of GDPR sections that are of particular importance.
That sums it up well. There are, without a doubt, a great number of DPA contract templates that can be found online. When looking for a template for a data processor agreement, you need to make sure that all of the necessary components are present. It will assist you in avoiding misunderstanding and removing potential dangers.
It is vital to keep in mind that it is preferable to spend some time customising a template rather than forgetting about important parts of the agreement.
Client Self-Assessment Guide
When considering outsourcing solutions, it’s crucial for clients to assess their needs and objectives. Here is a self-assessment guide to help businesses determine if the Safe Outsourcing Concept by Zeus is the right fit for them:
- Identify Your Business Goals: Clearly define your business objectives and innovation needs.
- Assess Your Internal Expertise: Evaluate your in-house expertise and determine whether additional specialised knowledge is required.
- Evaluate Your Risk Tolerance: Consider your organisation’s risk tolerance and the importance of data security in your industry.
- Analyse Your Resource Requirements: Determine whether you need to scale up or down for specific projects or activities.
- Review Your Budget: Assess your budget constraints and identify areas where cost efficiency can be improved.
- Consider Your Project Timelines: Determine whether project delivery timelines are a critical factor for your organization.
By following this self-assessment guide, businesses can gain a clearer understanding of their outsourcing needs and how the Safe Outsourcing Concept by Zeus can address those needs while delivering exceptional results.
In conclusion, the Safe Outsourcing Concept by Zeus represents a trusted path to innovation and growth. Its advantages, coupled with the self-assessment guide, provide a comprehensive framework for organizations to make informed decisions and harness the power of outsourcing for their continued success in today’s competitive business landscape.
Checklist for Choosing a Secure Data Processor
The following are the questions that should be asked:
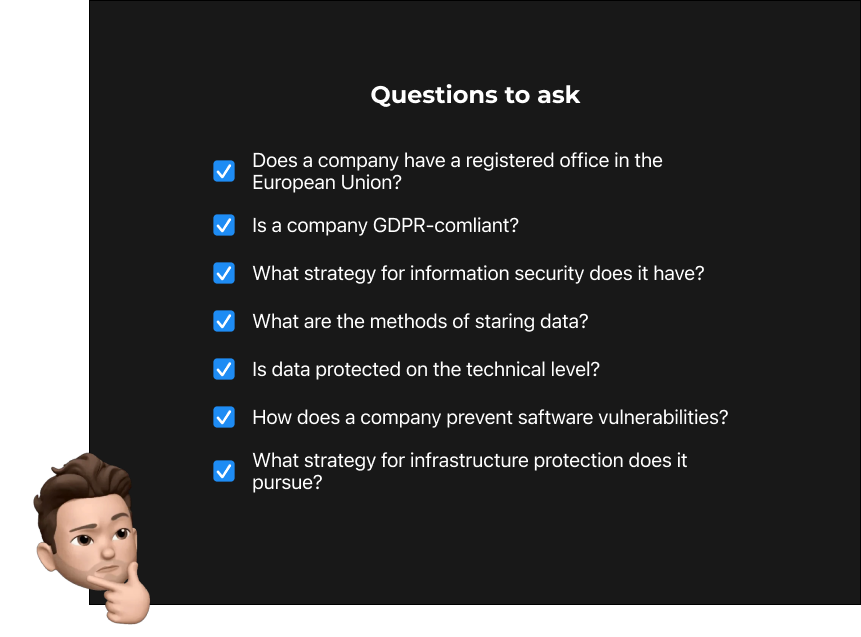
You are already familiar with the structure of an effective Data Processing Agreement. However, before you go ahead and sign the agreement, you need make sure that your software development partner can be trusted. Utilising our brief checklist might assist you in locating the problematic aspects of your data processor and ensuring that these issues are addressed in the DPA agreement.
1. Does a company have a registered office in the European Union?
Select a business outsourcing partner who has a physical presence in a member state of the European Union. It will provide you with more assurance regarding the safety of the services provided by your partner. Additionally, it will assist you in making certain that GDPR compliance and data protection are not just on paper but also in actual operation inside your organisation.
2. Is a company GDPR-compliant?
Investigate the vendor’s privacy and data protection policies as a first step. Verify the list of the outside entities who have permission to access the company’s data. Discuss the issues in advance in the event that you have any concerns regarding the level of security. When possible, it is in everyone’s best interest for the agreement or contract to provide a summary of any contentious areas.
3. What strategy for information security does it have?
Ask your potential business partner about the steps they take to protect sensitive information. Do they have a plan for the organisation’s safety? Inquire with them about who in their firm is in charge of maintaining the data’s safety. You need to determine whether or not your partner is ready to answer concerns about safety and protection.
4. What are the methods of storing data?
If a firm cannot guarantee the protection of its own data, it is extremely difficult for them to guarantee the safety of the data they collect about their customers. Inquire with your partner as to the location of their data storage. Do they utilise a storage method that is local to their location or one that is hosted in the cloud? In the event that they utilise the latter, how dependable is the cloud provider they use?
5. Is data protected on the technical level?
Inquire with the organisation that handles the outsourcing about the technical aspects of data protection. What kinds of tools and equipment do they use? How do they guarantee a safe authorisation process? A trustworthy partner will both oversee the inventory and keep a record of the devices that have been approved.
6. How does a company prevent software vulnerabilities?
When producing a software product, a professional software development team will adhere to the full-cycle process. That is to say, in addition to manufacturing the product itself, a corporation also offers support and maintenance services. To answer your question, how does your partner assure the safety of the items they manufacture? Do they have a plan of action ready to implement in the event that a data breach is reported?
7. What strategy for infrastructure protection does it pursue?
The last question can help you gain a better understanding of the company’s approach to the prevention of data breaches. Describe the data backup procedures that your potential partner uses. What measures do they take to prevent malicious assaults on their devices?
And What about Servers and GDPR?
When it comes to server location and the General Data Protection Regulation (GDPR), there are several important considerations to keep in mind. GDPR is a comprehensive data protection regulation enacted by the European Union (EU) to safeguard the personal data of EU residents. If your business or organization handles personal data of EU residents, regardless of where it’s based, you need to comply with GDPR. Here’s how server location factors into GDPR compliance:
- Data Processing Location: GDPR doesn’t specify the exact location where servers should be located. Instead, it focuses on the protection of personal data during processing. Organizations are required to ensure that personal data is processed securely and in compliance with GDPR, regardless of the server’s physical location.
- Data Transfer Restrictions: GDPR does regulate the transfer of personal data outside the European Economic Area (EEA). To transfer data to countries outside the EEA, you must ensure an adequate level of data protection or use safeguards like Standard Contractual Clauses (SCCs) or Binding Corporate Rules (BCRs).
- Third-Party Processors: If you use third-party data processors or cloud service providers, it’s essential to choose providers who are GDPR-compliant and have robust data protection measures in place. Ensure that they meet GDPR requirements even if their servers are located outside the EEA.
- Data Minimisation: GDPR emphasises the principle of data minimisation, which means you should only collect and store the data necessary for the purpose you’ve specified. Therefore, the location of your servers should align with this principle.
- Security Measures: The physical location of your servers should have adequate security measures to protect personal data from breaches or unauthorised access. This includes encryption, access controls, and regular security assessments.
- Notification of Data Breaches: GDPR requires organisations to report data breaches to the appropriate authorities and affected individuals within a specific timeframe. Regardless of server location, you must be able to fulfil this requirement.
In summary, the specific server location isn’t the primary focus of GDPR compliance. What’s essential is that organizations handling personal data of EU residents take the necessary steps to protect that data, regardless of where their servers are located. Complying with GDPR involves a combination of technical, organizational, and legal measures to ensure the security and privacy of personal data. It’s advisable to seek legal counsel or data protection experts to navigate GDPR compliance effectively.